During the HCL Connections Component Pack 8.0 CR8 update, some security settings are modified for the MongoDB replica set used by the HCL Connections Component Pack. This is managed by the check-and-update-mongo5-security Kubernetes (K8s) job, which creates the check-and-update-mongo5-security-* pod to change the security settings of the replica set. Once the job completes successfully, the K8s pod and the corresponding job are marked with the status complete(d) (see the attached screenshot).
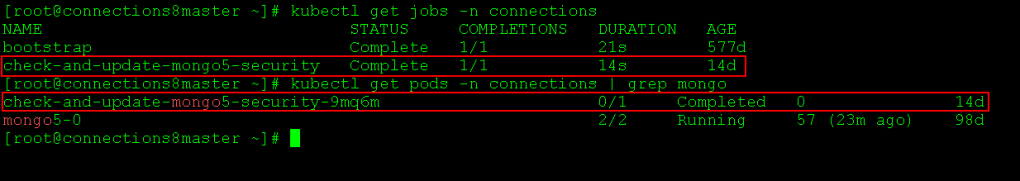
However, in one of the HCL Connections environments I am working on, the job didn’t complete successfully. During my initial analysis, I found the following error in the log of the check-and-update-mongo5-security pod:
MongoServerError: not primary and secondaryOk=false - consider using db.getMongo().setReadPref() or readPreference in the connection string
Upon further investigation, it became apparent that the check-and-update-mongo5-security pod was executing commands via the MongoDB shell that were only possible on a primary member of the MongoDB replica set. The failure occurred because the pod was connected to a secondary member.
Unlike my test environment, which uses only a single replica of the MongoDB instance, this environment’s K8s statefulset for MongoDB consists of three MongoDB replicas. In this setup, we have three MongoDB pods, of which only one can be the primary member of the MongoDB replica set, while the other two act as secondary members.
To resolve the issue, I followed the official guide in the MongoDB documentation to promote the mongo5-0 pod to become the primary member. After rerunning the Helm “infrastructure” chart for the HCL Connections Component Pack deployment, the K8s job check-and-update-mongo5-security completed successfully, allowing us to proceed with the update.
You can use the following kubectl command to connect to a MongoDB instance:
kubectl -n connections exec -it mongo5-0 -c mongo5 --\mongosh --tls --tlsCertificateKeyFile /etc/mongodb/x509/user_admin.pem \--tlsCAFile /etc/mongodb/x509/mongo-CA-cert.crt \--host mongo5-0.mongo5.connections.svc.cluster.local \--authenticationDatabase '$external' --authenticationMechanism MONGODB-x509
Hope this helps!
